In today’s rapidly advancing digital world, the importance of maintaining a secure and robust cybersecurity infrastructure cannot be overstated. Ensuring the optimal performance of a Security Operation Center (SOC) is crucial for the safeguarding of organizations, their data, and their assets. Central to this mission is the effective measurement and assessment of SOC performance.
In this informative blog post, we will delve into the critical SOC metrics that organizations must track to ensure that their security systems are functioning at peak efficacy, as well as identifying potential areas for improvement. From incident response times to SOC team productivity, understanding these key performance indicators will equip you with valuable insights into the overall health of your cybersecurity defenses.
Security Operation Center Metrics You Should Know
1. Number of events/incidents
This metric measures the total number of security events or incidents detected and managed by the SOC. It helps in understanding the overall efficiency of SOC and the volume of threats the organization is facing.
2. Incident response time
This metric measures the time taken by the SOC team to respond to a detected security incident. It helps in determining the effectiveness of the incident response processes and ensuring timely mitigation of threats.
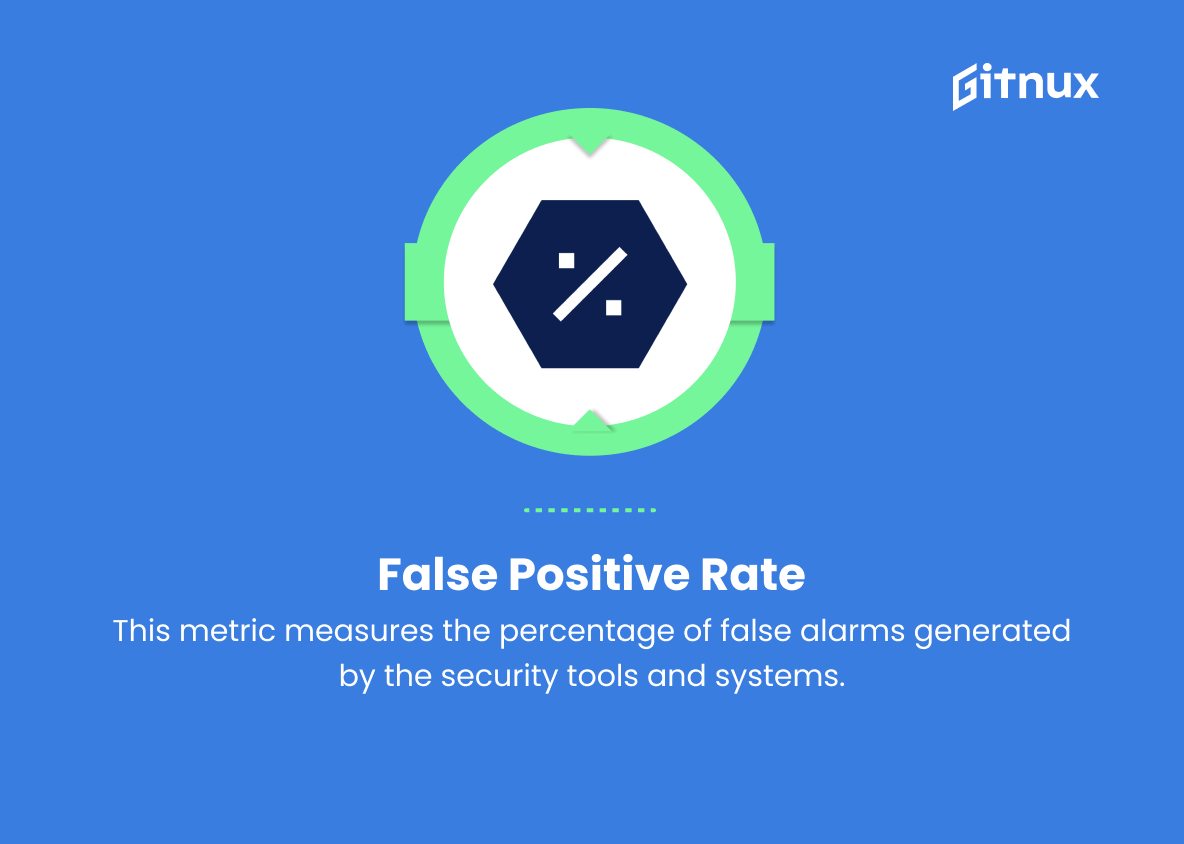
3. False positive rate
This metric measures the percentage of false alarms generated by the security tools and systems. A high false positive rate may result in inefficiency and resource wastage in the SOC, while a low false positive rate indicates effective threat detection systems.
4. Mean time to detect (MTTD)
This metric measures the average time taken by the SOC team to identify potential security threats. A low MTTD is crucial to minimize the damage caused by security breaches.
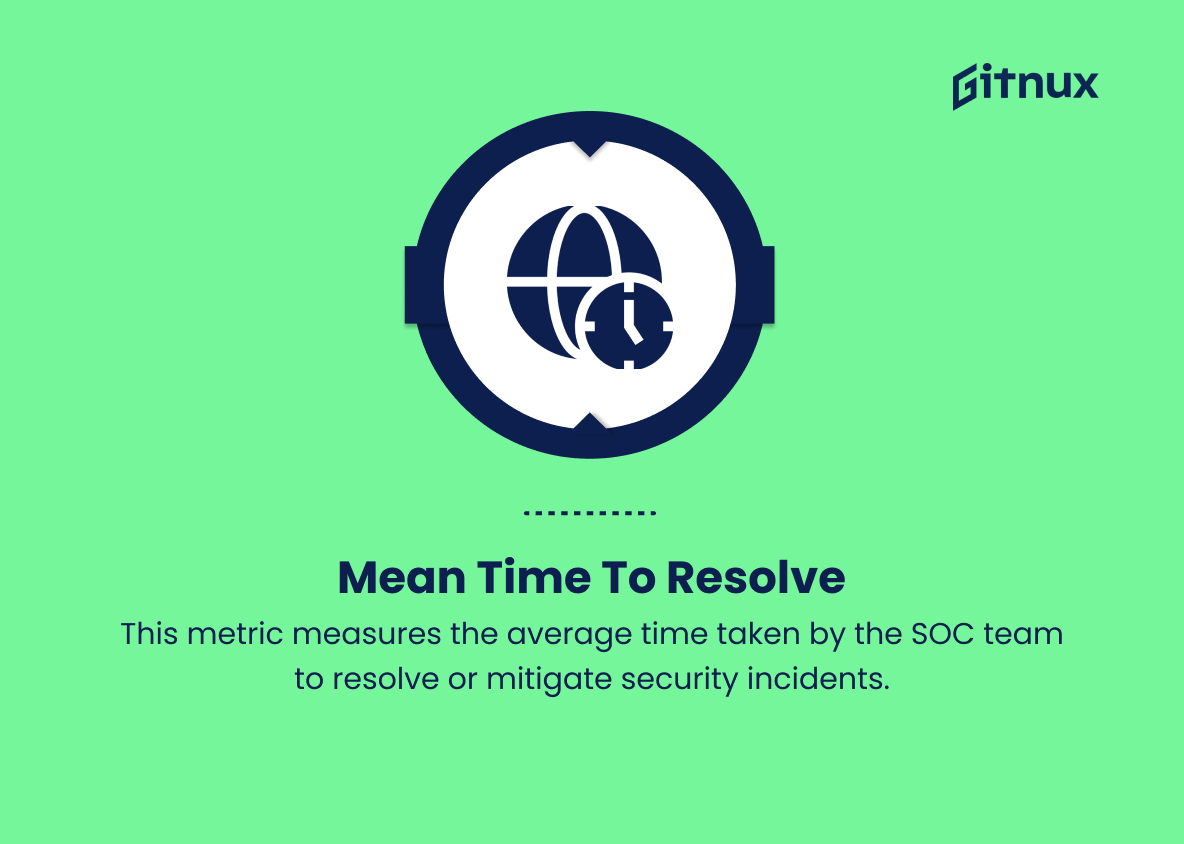
5. Mean time to resolve (MTTR)
This metric measures the average time taken by the SOC team to resolve or mitigate security incidents. A lower MTTR is indicative of a faster and more efficient incident resolution process.
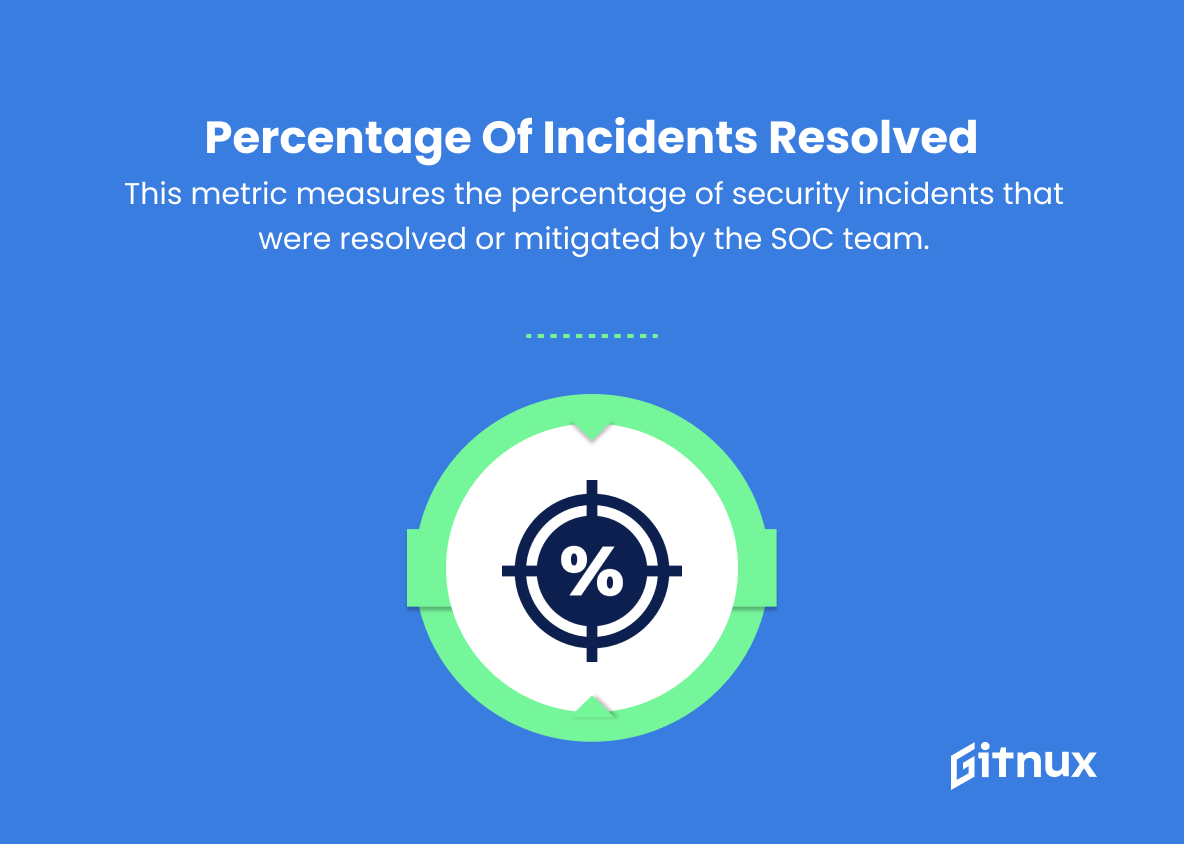
6. Percentage of incidents resolved
This metric measures the percentage of security incidents that were resolved or mitigated by the SOC team. It helps in assessing the overall effectiveness of the incident response process.
7. First contact resolution rate
This metric measures the percentage of incidents that are resolved in the first contact by the SOC team, without requiring a lengthy investigation. A high first contact resolution rate indicates an efficient SOC.
8. Incident classification accuracy
This metric measures the accuracy of incident classification done by the SOC team. Accurate classification helps in prioritizing incidents and allocating resources effectively.
9. Compliance score
This metric measures the level of adherence to various security standards, regulations, and policies by the organization. It helps in determining if the SOC is effectively contributing to the overall security posture of the organization.
10. SOC staff turnover rate
This metric measures the rate at which SOC analysts leave the organization. A high turnover rate may indicate low job satisfaction, poor working conditions, or other issues that can hamper the overall performance of the SOC.
11. SOC staff training hours
This metric measures the number of training hours allocated for SOC analysts’ skill development. Continuous training helps in keeping the SOC team updated with the latest threat intelligence and security best practices.
12. Security tool effectiveness
This metric measures the effectiveness and efficiency of the security tools and technologies deployed in the SOC. It helps in identifying areas where investments in tooling or improvements in security processes need to be made.
13. Post-incident review completion rate
This metric measures the percentage of security incidents that have a thorough post-incident review performed. Post-incident reviews help identify root causes, lessons learned, and areas for improvement in the SOC’s incident response process.
Security Operation Center Metrics Explained
The importance of Security Operation Center (SOC) metrics lies in evaluating the efficiency and effectiveness of an organization’s security measures. Tracking the number of events/incidents provides insights into the volume of threats and overall SOC performance, while incident response time assesses the speed and effectiveness of the response process. False positive rate, mean time to detect, and mean time to resolve all play crucial roles in determining the efficiency of threat detection systems and incident resolution capabilities.
Moreover, the percentage of incidents resolved, first contact resolution rate, and incident classification accuracy all contribute to understanding the overall effectiveness of the SOC’s response processes. Furthermore, compliance score and SOC staff turnover rate help ensure adherence to security standards and maintain a stable, knowledgeable workforce. Investment in SOC staff training hours is essential for continuous skill development and staying updated with the latest threat intelligence.
Lastly, security tool effectiveness and post-incident review completion rate are key factors in identifying areas for improvement and ensuring optimal security processes within the organization. By keeping track of these SOC metrics, organizations can enhance their overall cybersecurity posture and minimize the risk of security breaches.
Conclusion
In summary, Security Operations Center (SOC) metrics play a pivotal role in evaluating the efficiency and effectiveness of an organization’s cybersecurity posture. A comprehensive and well-structured set of metrics enable better decision-making, resource allocation, and continuous improvement in security operations. As cyber threats continue to evolve, it is crucial for businesses to establish a robust set of SOC metrics to stay ahead of the curve and mitigate risks proactively.
By continuously monitoring, analyzing and refining these metrics, organizations can bolster their cybersecurity defenses and improve their overall resilience in the face of ever-increasing cyber threats. Remember, a solid measurement framework paired with timely and accurate reporting not only strengthens the backbone of any SOC but also ensures the ongoing success and sustainability of your organization’s cybersecurity program.