In the vast realm of data exploration and analysis, a unique field of interest is emerging and garnering attention – Hacker Statistics. This fascinating realm may evoke images of stealthy individuals typing away at their computers in dimly-lit rooms. However, it’s far from this Hollywood-inspired representation. Rather, Hacker Statistics explores ingenious problem-solving methods used to understand complex data-driven problems.
This blog post aims to demystify Hacker Statistics, unravel its methods, and examine its vital importance in the current data-centric world. Join us as we venture into this captivating discipline, where the explorer’s mindset meets data science, all within the boundary of statistical understanding.
The Latest Hacker Statistics Unveiled
43% of cyberattacks are aimed at small businesses, but only 14% are prepared to defend themselves.
Drawing upon the statistics, we walk a tightrope over a concerning reality that jolts the world of small businesses; 43% of cyberattacks target these very enterprises. Deserting the realm of cybernetic tranquility, they find themselves amid a damaging tempest, still unprepared, as indicated by the mere 14% braced for such an onslaught.
In the labyrinth of hacker statistics, this fact braids a tale of vulnerability, negligence, and possible devastation, holding a mirror to small businesses. It points to an urgent need for bolstered cyber defenses and awareness, particularly for those pint-sized market players who, despite being the preferred bait for cyber predators, are lagging in protective measures.
This piece of statistical reality is like a glaring red signal on the dashboard of an automobile. Ignoring it could steer us towards dangerous landscapes, making it a cardinal element in the narrative woven in a blog post about Hacker Statistics. The purpose of tracking these numbers shines a flashlight on the harsh truth small businesses face and the urgency to armor themselves appropriately against the looming threat of cyberattacks.
Approximately 30,000 websites are hacked every day.
As we navigate through the digital labyrinth, the staggering figure of around 30,000 websites falling prey to hackers each day serves as a flashing neon sign of the ubiquitous nature of cyber threats. It invigorates the essence of our blog post about Hacker Statistics by accentuating the intensity and the scope of cyber lawlessness chillingly enveloping the web. This figure not only assists in understanding the prevalence of individual potential to endure a cyber attack, but it also paints a vivid picture of the unrelenting encounters between keyboard warriors and cyber adversaries in the world wide web.
This high volume statistic becomes a lifeblood pulsating undeniable urgency within our discussion, helping us chart the gravity of the cyber-crime landscape, while fostering a more insightful exploration of defensive strategies, detection systems and the evolution of hacking methods. It emphasizes the undebatable need for constantly evolving cyber security measures and underscores the value of awareness about the scale of this ever-looming digital peril.
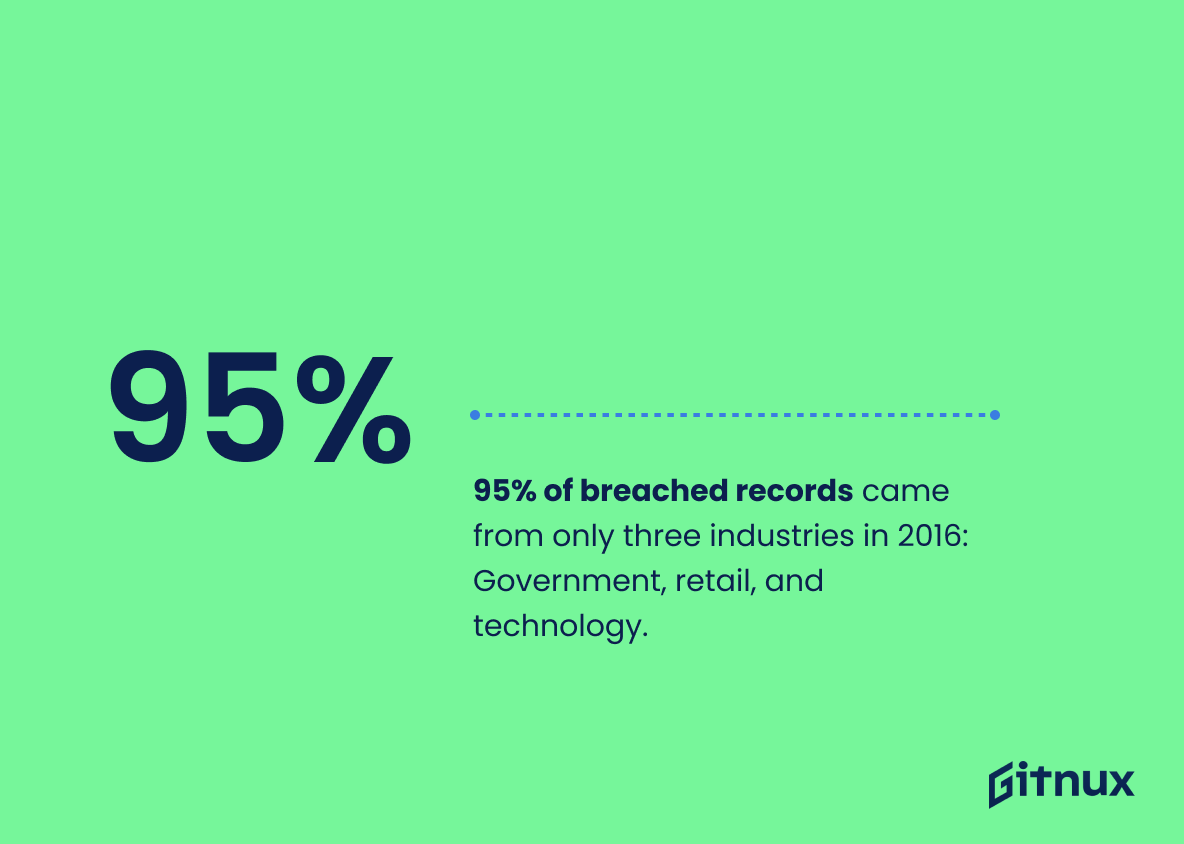
95% of breached records came from only three industries in 2016: Government, retail, and technology.
Examining this compelling statistic in the realm of hacker statistics takes us on a revealing journey. It thrusts into sharp relief the fact that in 2016 a staggering 95% of breached records originated from just three sectors: Government, Retail, and Technology. This served as a stark revelation of the disproportionately high vulnerability of these sectors to cyberattacks.
This observation is akin to a red flashing beacon, highlighting the urgent need for stronger network fortification and data protection in these particular industries. Furthermore, it showcases the favored hunting grounds for cyber predators, providing invaluable understanding to cybersecurity units in these industries. Hence, this alarming statistic undeniably anchors the essence of this blog on hacker statistics.
Every 39 seconds, there is a hacker attack.
Painting a vivid picture of the dynamic and high-stakes world of cyber security, the staggering statistic reveals that a cyber attack occurs every 39 seconds. Located at the heart of this digital battlefield, it relentlessly sheds light on the relentless and relentless speed of these invasive assaults.
It thereby underscores the urgency of understanding and employing hacker statistics in the blog post, aiming to provide the reader with an armor of knowledge against this invisible adversary. The frequency of these attacks is an eloquent reminder of needs to not only highlight the magnitude of the problem but also stimulate proactive action and strategic thinking in the realm of cyber-defense.
More than 77% of companies do not have a consistent cybersecurity response plan.
Painting the stark reality of the cybersecurity landscape, the statistic reveals a worrying vulnerability of modern companies – over 77% of them are unprepared for a consistent response to potential cyber threats. In the unforgiving battleground of the digital world, where hackers and cybercriminals constantly evolve tactics, this statistic rings as a chilling wake-up call.
The essence of this number unveils the precarious position that companies stand in, racing against intruders, yet, bewilderingly, still lacking a robust cyber defense. Highlighting the need for companies to foster a proactive cybersecurity culture and to invest in comprehensive response plans, this figure becomes a vital piece of the jigsaw puzzle in understanding both the prevalence of hacking and the urgent necessity for increased corporate vigilance.
In 2019, 62% of businesses admitted to experiencing phishing attacks.
Peeling back the apparent layers of security, in 2019, a startling 62% of businesses admitted to experiencing phishing attacks. This statistic paints an alarming picture for the blog’s topic about Hacker Statistics. It serves as a stark revelation and underscores the prevalence and dangers of cyber-security threats in the contemporary business landscape.
It shines a light on the fact that hackers have channelized their illicit craft not just towards individual email accounts but also towards the much larger and potentially more rewarding targets of businesses. With more than half of businesses reporting such incidents, it also stirs reader curiosity about the methods employed by hackers and the steps businesses must take for strengthened digital security.
The majority of hackers take up to 24 hours to steal data from a system after gaining access.
In the digital battlefield where hackers and security professionals continually vie for supremacy, every minute is precious. The statistic that most hackers can raid data within 24 hours from breaching access is a spotlight illuminating a significant vulnerability in our systems. Directly pertinent to a blog post about Hacker Statistics, this metric underlines the urgency of swift identification and rectification of breaches.
It suggests that the window to counteract a security intrusion is surprisingly small. Furthermore, it underscores the importance of having robust, continuous monitoring systems in place while promoting an in-depth understanding of ‘hacker-hours’, a timeline showing that our defenses have to stay vigilantly ahead of the menace by not just days, but hours.
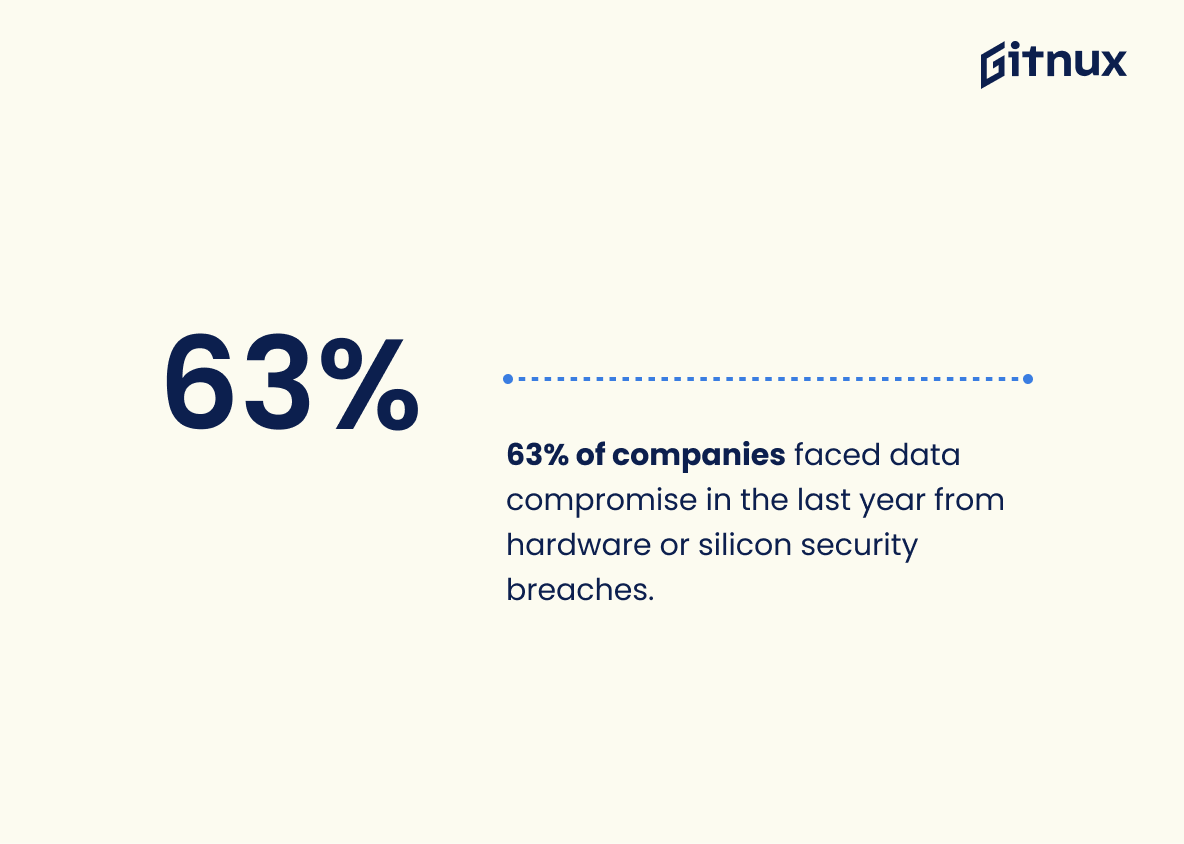
63% of companies said their data was potentially compromised within the last twelve months due to a hardware- or silicon-level security breach.
In the fascinating world of hacker statistics, this nugget of information—the fact that 63% of companies reported potential data compromises in the last year due to hardware or silicon-level breaches—serves as a stark wake-up call. It bares a worrisome paradox: even as companies secure their cyberspace front door, vulnerabilities might be embedded deep within their hardware back house.
From a statistical perspective, it emphasizes the reality that cyber threats are no longer exclusive to the realms of software and network breaches; the battlefields are shifting, and alarmingly so to a specter that is perhaps more challenging to ward off. Interesting, isn’t it? While every statistic tells a story, this one paints a particularly vivid picture of modern threat landscapes—where hardware, the literal backbone of our digital era, might be the most treacherous Trojan horse of all, carrying within its silicon heart something that could bring colossal corporations to their knees.
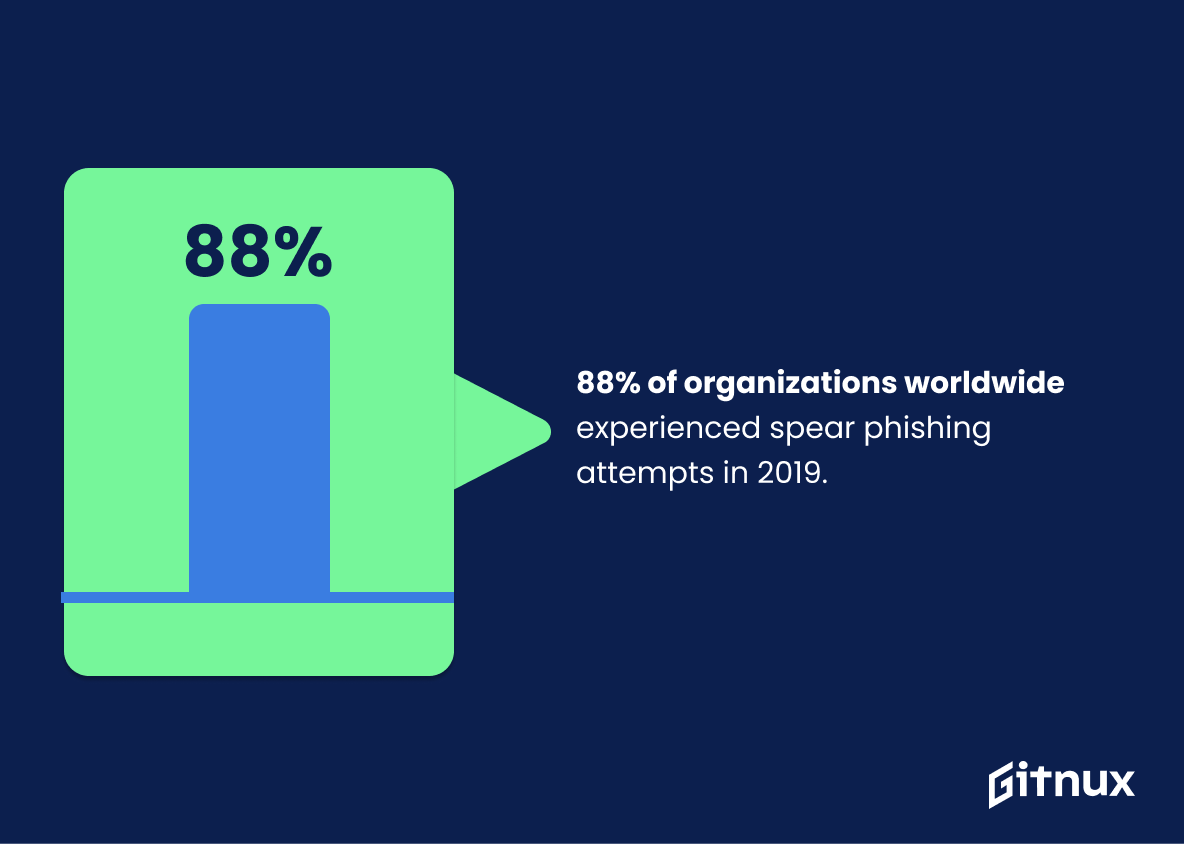
88% of organizations worldwide experienced spear phishing attempts in 2019.
Delving into the intriguing realm of Hacker Statistics, one cannot sideline the compelling fact that within the span of 2019 alone, a staggering 88% of organizations worldwide fell prey to spear-phishing attempts. Now, this is not merely a bland percentage, sitting abstractly on a pie chart; rather, it’s a cyber-siren warning the digital world of the unremitting exposure to potential risks.
This impersonal percentage represents countless hours of lost productivity, significant financial losses, and compromised reputations. It underlines the paramount need for robust digital security measures, proactive phishing detection, and user education. Essentially embodying the frontline trench battle of cyber warfare, the growing onslaught of spear-phishing attacks, as revealed by this statistic, forms the crux of any discourse on Hacker Statistics.
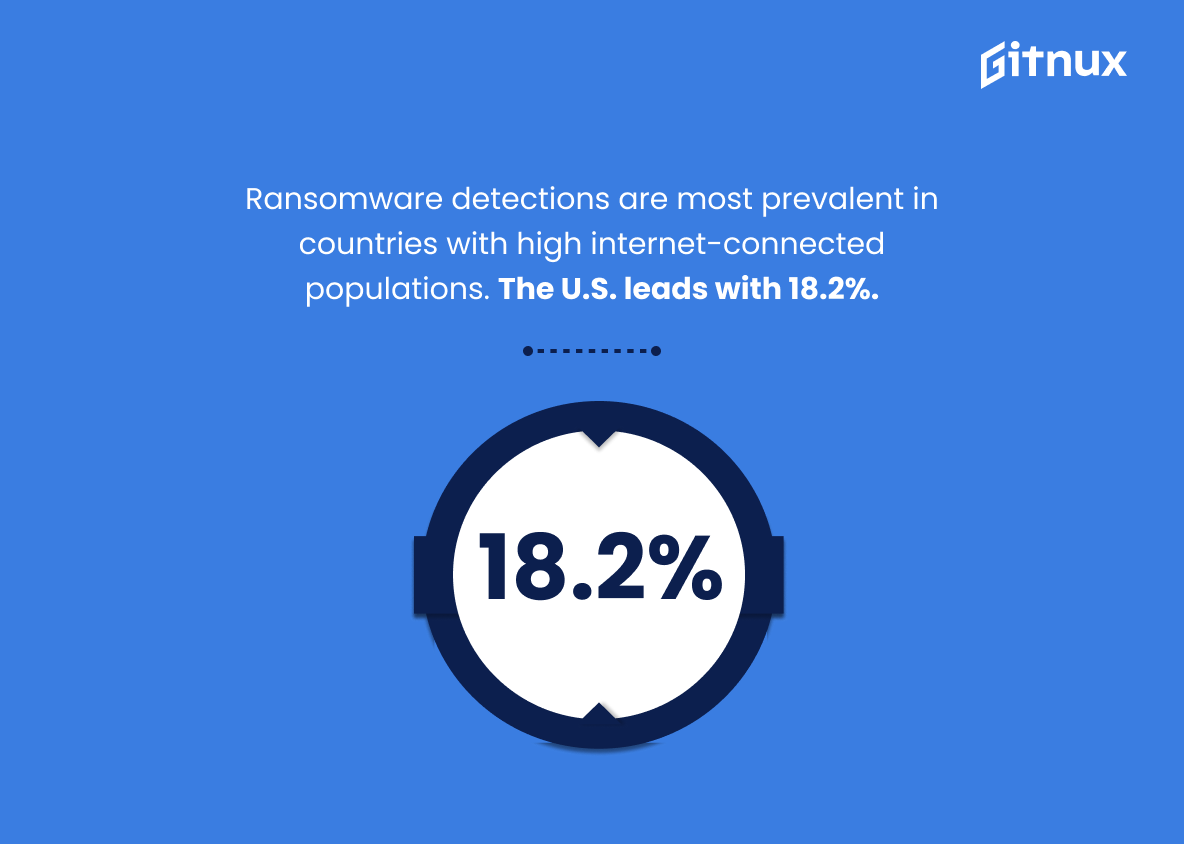
Ransomware detections have been more dominant in countries with higher numbers of internet-connected populations. The U.S. ranks highest with 18.2%
Delving into the digital world of hacker statistics, we encounter an intriguing correlation where higher numbers of internet-connected populations in countries seem to be directly proportional to an increase in ransomware detections. Painted with a broad brush, the U.S. unanimously steals the spotlight, leading on this frontline with a substantial share of 18.2%.
Through these statistics, a narrative unfolds about the interplay between internet proliferation and cybercrime, more specifically ransomware, a preferred tool in a hacker’s arsenal. It shines a light on the heightened vulnerability of nations with larger online communities, offering a crucial perspective for those interested in understanding the dynamics of the cyber world.
This statistic is akin to a compass in the vast expanse of cyber threat landscapes. It not only guides cybersecurity strategies and measures, but also becomes an imperative conversation starter about managing technology risks in socially and technologically advanced societies, like the U.S. Undoubtedly, these figures are paramount to understanding the gravity and global distribution of cyber threats, an invaluable addition to the discourse on hacker statistics.
Businesses lost over $1.8 billion in 2020 as a result of business email compromise scams.
Highlighting an astonishing $1.8 billion loss in 2020 due to business email compromise scams thrusts the menacing reality of cybercrime into the limelight. This astounding figure underscores the gravity of hacker activities, painting a vivid picture of the financial hemorrhage that businesses, regardless of size or industry, can suffer at the hands of digital saboteurs. As we delve deeper into the realm of hacker statistics, this information serves as both a stark warning and a call-to-arms for organizations to invest vigorously in data protection measures.
Not only does it expose the potential financial catastrophe lying within deceptive emails, but it also stands as a testament to the increasingly sophisticated and audacious exploits of cybercriminals in the digital age. This jarring financial figure gives life to the often abstract world of cybersecurity, connecting the intangible threats lurking beneath innocuous appearing email messages to very tangible, very real financial loss.
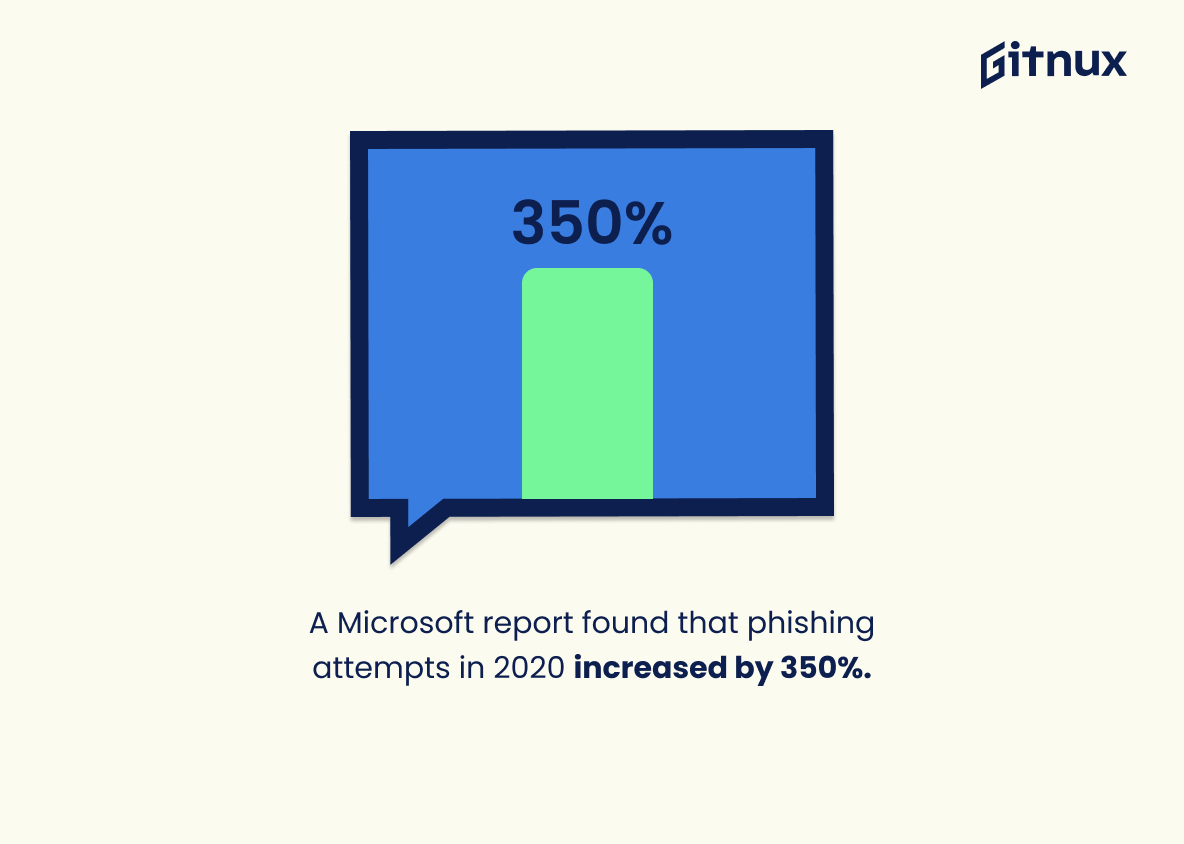
A Microsoft report found that phishing attempts in 2020 increased by 350%.
This dramatic influx of phishing attempts, according to the Microsoft report, throwing light on a 350% spike in 2020 serves as a deafening alarm for everyone. In the terrain of Hacker Statistics, it unravels the escalating severity and sophistication of cyber threats. It provides compelling evidence that hackers are growing more relentless and crafty in their strategies, utilizing phishing as a favored tool of deception. Weaving this into our narrative gives readers an acute sense of urgency to understand these statistics better and thereby, take necessary countermeasures to protect themselves in the increasingly treacherous digital landscape.
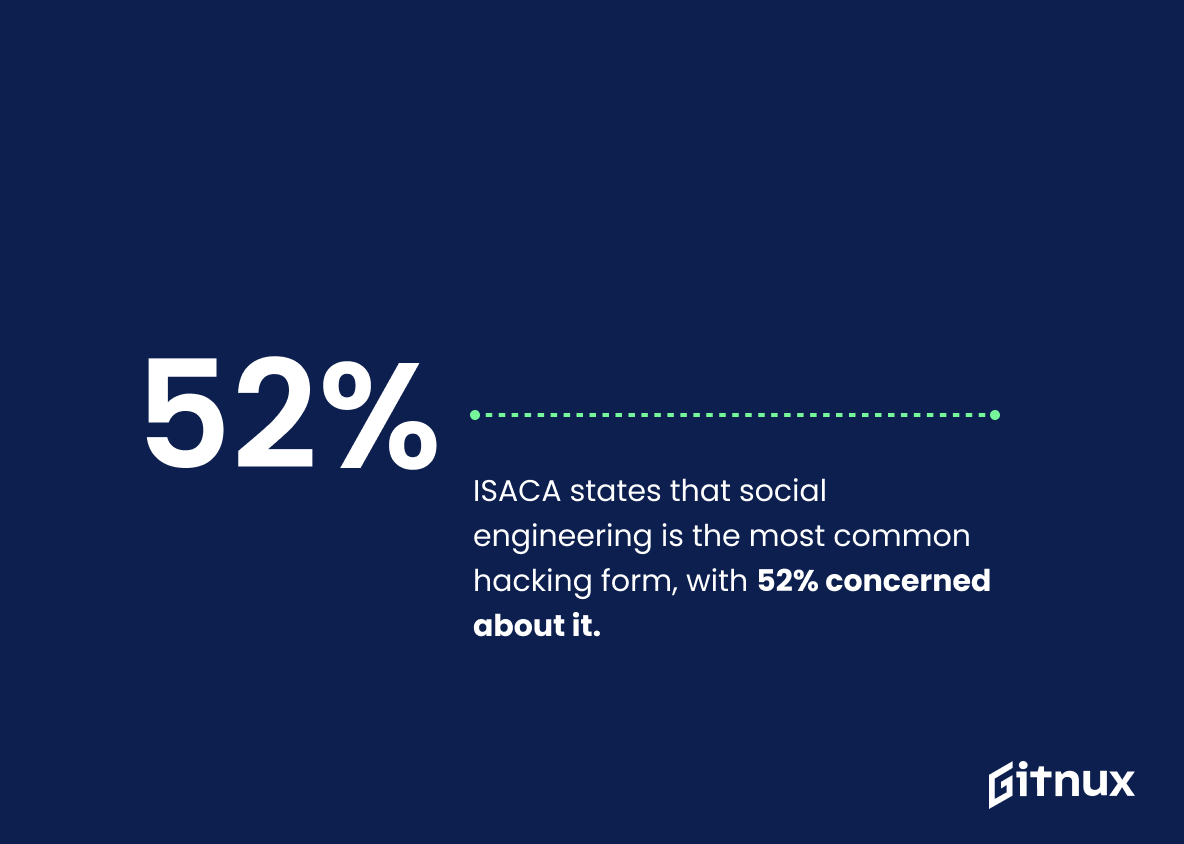
According to ISACA, the most common form of hacking is social engineering, with 52% of respondents indicating that it’s the biggest concern
Weaving this cogent datum into a blog post about Hacker Statistics implores readers to step back and view the landscape of cyber threats from a fresh perspective. With 52% of respondents from ISACA marking social engineering as their primary worry, we are reminded that hacking is not solely a breach in electronic barriers, but an exploitation of human psychology and trust as well. This highlights the urgency of equipping oneself with not just technical protective measures, but also knowledge about social manipulation techniques employed by hackers. This statistic encourages a dual focus on both technological and human defense mechanisms.
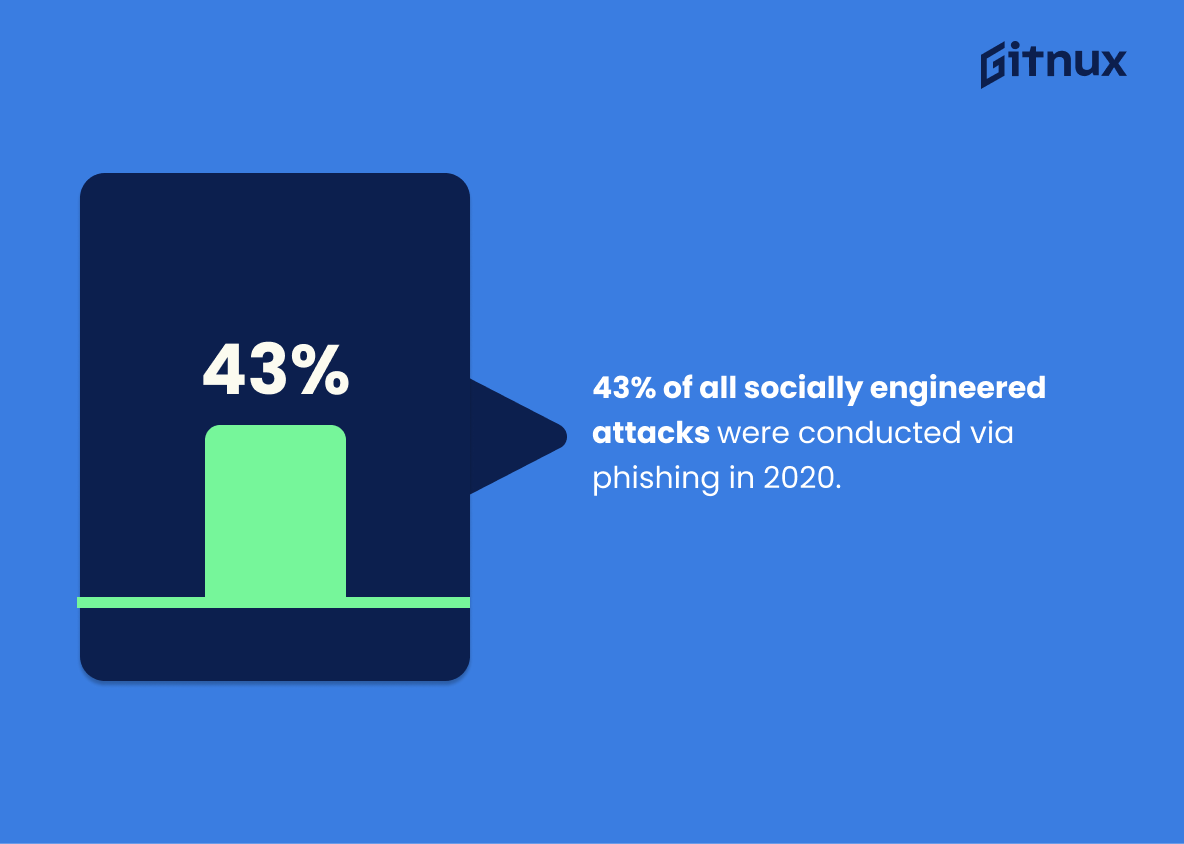
43% of all socially engineered attacks were conducted via phishing in 2020.
Undeniably, the landscape of cyber threats is continually evolving, reflected by the telling statistic stating 43% of all socially engineered attacks were implemented via phishing in 2020. Interpreting this illuminating information, our insightful blog post unfolds the staggering prominence of phishing as a hacker’s weapon of choice. This critical percentage serves as a powerful reminder for organizations to proactively focus their cybersecurity policies on preventable threats.
In the battlefield of the digital world, understanding these statistics equips us with a more precise lens to view the impending cyber threats, inevitably steering the discourse in Hacker Statistics towards more informed, insightful, and impactful perspectives.
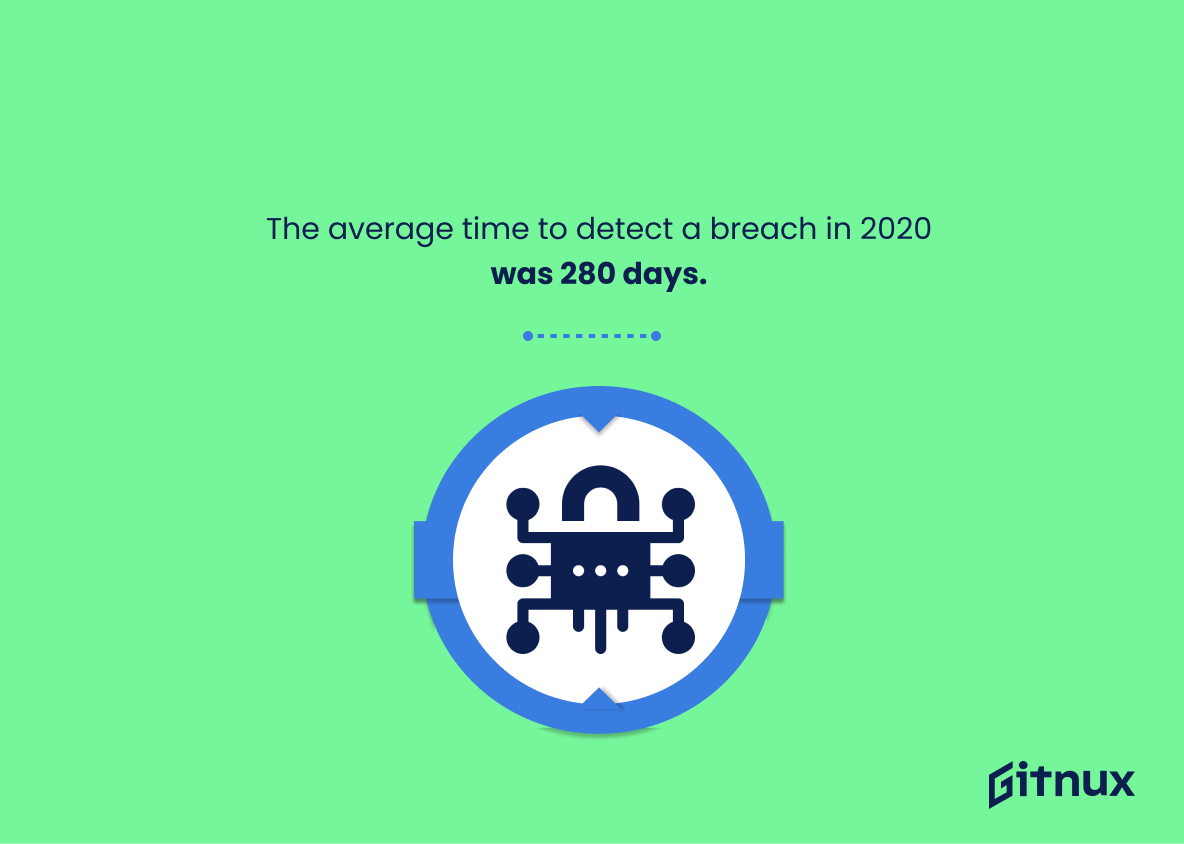
The average time to detect a breach in 2020 was 280 days.
Dramatizing the humbling revelation of 280 days as the average detection time for a breach in 2020 unearths an unsettling truth about cybersecurity. It underscores the stealth of contemporary hackers and the lagging reality of defense measures in the rapidly progressing digital battlefield. Skating all too dangerously on thin ice, organizations, suffused with a false sense of security, remain oblivious to intrusions for nearly nine months. This menacing quiescence from detection until reaction exposes them to potential voluminous data leaks, damaging reputation and shaking customer confidence to its core.
This disconcerting lapse practically gifts hackers a luxurious time buffer, a freedom for them to execute their agendas unhindered- be it data theft, ransomware attacks, or setting the stage for future exploit. In a realm where every second counts, this statistic echoes an alarm, a wake-up call for enterprises to advance their guard, hone their detection capabilities, and reduce this critical window of vulnerability.
In the throes of evolving hacker tactics, this statistic adroitly paints the picture of the current cybersecurity landscape, dictating the urgency of fortifying digital ramparts, fostering consumer awareness, and prompting a tireless pursuit for innovative countermeasures against these digital predators.
Nearly half (49%) of organizations surveyed faced a cyberattack at least once a month in the first half of 2021.
Diving into the digital catacombs of this statistic, one realizes that it paints a vivid picture of the perils of the internet era. With 49% of organizations standing as victims of monthly cyber-attacks in the initial six months of 2021, this insight elucidates the unyielding brute force of cyber criminals. It provides concrete numerical evidence of the cyber battles being fought behind the screens, demonstrating a relentless wave of invasions that shake the very foundations of organizational cybersecurity.
In the realm of Hacker Statistics, it stands as a stark reminder for companies to gird their cyber loins and strengthen their digital fortresses. The rhythm of this statistic reverberates the need for innovative and stringent cyber safety measures, bridging the gap between a blog post and its underlying message – that in the face of persistent online threats, the world needs more digital warriors, armed with knowledge and power of hacker statistics.
Global software exploitations rose by 49% in the first half of 2021.
In the intriguing world of hacker statistics, the incredible 49% rise of global software exploitations in the first half of 2021 serves as a flashing red beacon. It not only emphasizes the sharpening claws and enhancing skills of cybercriminals but also showcases the escalating vulnerabilities in arguably robust security systems around the world.
It’s akin to watching a suspense-filled movie where the antagonist suddenly gains an unexpected advantage, casting a shiver down the spine of those involved. This surge provides potent fodder for dialogue concerning the importance of advanced protective measures, technology updates and the necessity for users to be continuously cautious.
This electrifyingly high statistic draws the battle lines, marking the arena where the war against cybercrime plays out: the continuous coding and recoding of software programs. It forces us to acknowledge the brewing storm in the cyber world and the immediate need for effective strategic planning to weather it.
Ransomware increased 151% in the first half of 2021.
Highlighting the steep surge of Ransomware by 151% in the first half of 2021 unfurls a cautionary tale in the digital security landscape. In the realm of Hacker Statistics, this figure provides not merely numerical data, but it accentuates the preparedness—or lack thereof—of organizations and individuals to confront ever-evolving cyber threats.
Crucially, it underscores the aggressive escalation of hacker activities, specifically with ransomware, a malicious software that hackers deploy to encrypt and hold data hostage in exchange for a ransom. More than a percentage, these numbers represent disrupted businesses, compromised personal data, and financial losses.
In the chessboard of cybersecurity, it therefore serves as a grim reminder that hackers are always on the move, perpetually refining their strategies. For readers, such unnerving trends should act as the impetus to bolster one’s knowledge, promote the importance of robust digital security practices, and enhance defense mechanisms against such insidious threats.
Conclusion
As we wrap up our discussion on Hacker Statistics, it’s clear that this field extends far beyond simple computations. Its applications are vital in cyber warfare, security breaches prediction, network safety, and data protection. Understanding hacker statistics enables organizations to strengthen their informational infrastructure and safeguard digital assets, making it a pivotal aspect of contemporary cybersecurity strategies.
So whether you’re an aspiring IT professional, a statistician interested in cybersecurity, or a business owner looking to secure your online processes, a grasp of Hacker Statistics is certainly a practical, worthwhile tool in your arsenal.
References
0. – https://www.www.forbes.com
1. – https://www.www.cybintsolutions.com
2. – https://www.www.ibm.com
3. – https://www.www.proofpoint.com
4. – https://www.www.microsoft.com
5. – https://www.www.sonicwall.com
6. – https://www.www.securitymagazine.com
7. – https://www.breachlevelindex.com
8. – https://www.cybersecurityventures.com
9. – https://www.www.verizon.com
10. – https://www.www.ic3.gov
11. – https://www.www.isaca.org
12. – https://www.www.bromium.com
13. – https://www.theharrispoll.com
14. – https://www.www.symantec.com